What is SSH?
SSH (Secure Shell) is a cryptographic network protocol used for securely accessing and managing remote servers over an unsecured network. Developed in 1995 as a replacement for Telnet, SSH ensures encrypted communication between a client and a server.
Key Features of SSH:
Encrypted data transmission
Secure user authentication
Secure tunneling and port forwarding
Remote command execution
Why Use SSH?
The growing need for security in remote access protocols has made SSH the de facto standard in system administration, cloud computing, and network engineering.
Benefits of SSH:
Prevents credential interception
Supports passwordless logins via keys
Enables encrypted file transfers (SCP/SFTP)
Allows secure automation and remote scripting
How SSH Works: Step-by-Step
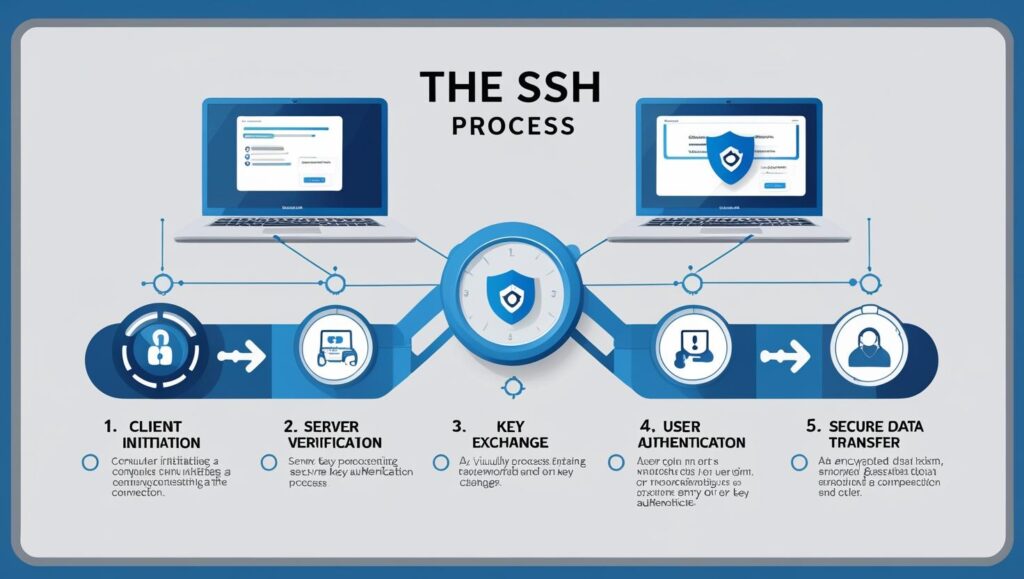
Let’s break down how SSH works step by step to understand the connection process.
1: Client Initiation
The SSH client (e.g., PuTTY, Terminal) initiates a connection by contacting the server over port 22.
2: Server Identity Verification
The client verifies the server’s public key against a known list of hosts to ensure it’s not connecting to a malicious machine.
3: Key Exchange and Session Setup
A secure session is negotiated using key exchange algorithms to ensure future communication is encrypted.
4: User Authentication
Depending on the configuration, the user authenticates via password, public/private keys, or other mechanisms.
5: Secure Data Transmission
Once authenticated, the session allows encrypted command execution or file transfers.
SSH Protocol Components
To fully understand the protocol, you need to know its building blocks.
1. Transport Layer Protocol
Handles initial key exchange, server authentication, encryption, and data integrity.
2. User Authentication Protocol
Supports public key, password, Kerberos, and host-based authentication.
3. Connection Protocol
Manages multiple logical channels like shell sessions, port forwarding, etc.
SSH Key Exchange Explained
SSH uses key exchange algorithms to establish a secure communication channel.
Popular Algorithms:
Diffie-Hellman (DH)
Elliptic Curve DH (ECDH)
RSA Key Exchange
These protocols ensure that even if someone intercepts the traffic, they cannot decipher the content without the private key.
How SSH Authentication Works
There are two common SSH authentication methods:
1. Password-Based Authentication
Simple but less secure; vulnerable to brute-force attacks.
2. Key-Based Authentication
Involves a public/private key pair, offering a much higher security level.
The client keeps the private key
The server stores the public key
The client proves possession of the private key to authenticate
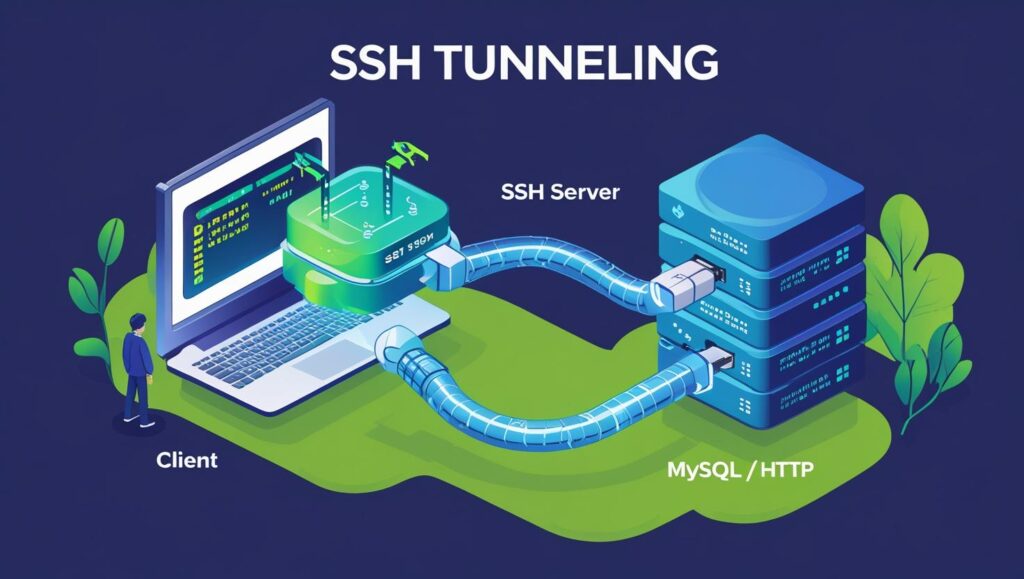
How SSH Tunneling Works
SSH tunneling allows secure forwarding of insecure protocols through encrypted channels.
Use Cases:
Secure database access
Encrypted web browsing via proxy
VPN-like functionality
Example:
A developer can access a remote MySQL database securely through an SSH tunnel without exposing port 3306 to the internet.
SSH vs Telnet: Key Differences
| Feature | SSH | Telnet |
|---|---|---|
| Encryption | Encrypted | Plain text |
| Authentication | Secure key-based login | Username/password only |
| Security | High | Low (deprecated) |
| Use Today | Widely used | Rare, for legacy systems |
Common Use Cases for SSH
- Managing remote servers and IoT devices
Secure file transfer using SFTP/SCP
Automated deployments (CI/CD)
Secure Git operations (e.g., GitHub over SSH)
Tunneling insecure traffic through encrypted channels
Conclusion
Understanding how SSH works is essential for anyone involved in system administration, cloud computing, or cybersecurity. With its robust encryption, flexible authentication, and versatile tunneling features, SSH remains the backbone of secure remote communication.
By integrating best practices such as key-based authentication and secure tunneling, you can safeguard your infrastructure against modern cyber threats.